Loading...
Cybersecurity in vehicles and fleets: Risks, impacts and solutions
In today’s hyper-connected transportation landscape, cybersecurity is no longer a back-office IT concern, it’s a frontline operational priority. Fleet operators increasingly rely on digital tools such as telematics, GPS tracking, electronic logging devices (ELDs), and cloud-based fleet management systems. While these technologies enhance efficiency, safety, and compliance, they also introduce a wide array of cyber vulnerabilities that can disrupt operations, compromise sensitive data, and inflict significant financial and reputational damage.
The expanding digital footprint of fleet operations
Modern fleets are powered by a digital ecosystem that includes:
- Fleet Management Software (FMS) for dispatch, location, routing, and maintenance tracking
- Telematics Systems for real-time vehicle diagnostics, driver behavior monitoring, and specialty information such as cargo temperature
- ELDs for regulatory compliance and hours-of-service tracking
- Mobile Apps used by drivers for communication, navigation, and reporting
- Cloud Platforms for data storage and analytics
Each of these components represents a potential attack surface for cybercriminals.
Vehicle attack surfaces: Where fleets are vulnerable
As vehicles become more connected, they also become more exposed to cyber threats. Key attack surfaces include:
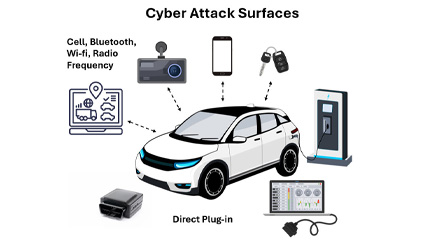
- Telematics Control Units (TCUs): These devices collect and transmit vehicle data. If compromised, attackers could manipulate vehicle diagnostics or location data.
- Onboard Diagnostics Ports: Used to connect engine diagnostic equipment and telematics hardware, these ports can be exploited to inject malicious code or extract sensitive data.
- Infotainment and Navigation Systems: These systems often connect to mobile devices and the internet, creating potential entry points for malware.
- Vehicle-to-Everything (V2X) Communication: As fleets adopt smart infrastructure, V2X systems can be targeted to disrupt vehicle coordination or traffic flow.
- Mobile Devices and Apps: Drivers’ smartphones and tablets, if not properly protected, can serve as gateways to fleet systems.
- Cloud-Based Platforms: Centralized data storage and analytics platforms are attractive targets for ransomware and data breaches.
- Vehicle charging: Electric vehicles have additional exposure while connected to a charging station, particularly at public charging facilities.
Real-world impacts of cyber incidents
Cyberattacks on fleet operations can have severe consequences:
- Operational Downtime: A ransomware attack can paralyze dispatch systems, stranding vehicles and delaying deliveries and services.
- Data Breaches: Exposure of driver records and biometrics, financial systems, customer data, and proprietary logistics information can lead to legal and reputational fallout.
- Financial Losses: Costs may include ransom payments, system recovery, legal fees, regulatory fines, and increased insurance premiums.
- Reputational Damage: Clients and partners may question a company’s ability to safeguard data and maintain service continuity.
Strengthening cybersecurity: Key certifications
To build a robust cybersecurity framework, fleet operators can pursue industry-recognized certifications that validate their security posture and demonstrate a commitment to best practices.
- ISO/IEC 27001: This international standard provides a framework for establishing, implementing, and maintaining an Information Security Management System (ISMS). It helps organizations identify risks, implement controls, and continuously improve their cybersecurity defenses.
- SOC 2 (System and Organization Controls): SOC 2 certification is essential for companies that manage customer data in the cloud. It evaluates controls related to security, availability, processing integrity, confidentiality, and privacy.
- NIST Cybersecurity Framework: Developed by the U.S. National Institute of Standards and Technology, this framework offers a flexible, risk-based approach to managing cybersecurity. While not a certification, aligning with NIST standards is often required for government contracts and large enterprise partnerships.
- Cyber Essentials (UK): This UK government-backed certification demonstrates basic cybersecurity hygiene and is often required for public sector contracts. It’s a good starting point for companies looking to build foundational security practices.
- CIS Controls: The Center for Internet Security (CIS) provides a prioritized set of actions to protect organizations from common cyber threats. Implementing these controls can help prepare for audits and certifications.
Best practices for fleet cybersecurity
In addition to certifications, fleet operators should adopt the following best practices:
- Conduct a fleet cyber audit: Identify all hardware, software, special equipment and third parties involved in your fleet operations; review attack surfaces. Utilize the services of cyber experts to assist in identifying threats and ensuring appropriate controls are in place.
- Segment Networks: Isolate vehicle systems from corporate networks where it is possible to limit the spread of malware.
- Update software regularly: Keep all systems and devices patched against known vulnerabilities.
- Use multi-factor authentication (MFA): Require MFA for accessing sensitive systems and data.
- Train Employees: Educate drivers and staff on phishing, password hygiene, and secure device usage. Remind employees to install security updates on their mobile devices which connect to the vehicle (Bluetooth, Wi-Fi, charging cable).
- Third-party management
- Only use software and hardware vendors that have good cyber security protocols in place, including maintaining certifications indicated above.
- Utilize reputable maintenance and repair facilities with cyber security procedures and certifications as they are plugging directly into your vehicles systems.
- Complete a cyber security audit of these third parties at least once a year.
- Back-ups: Ensure systems are backed up regularly to facilitate restoration.
- Incident response planning: Develop and test a response plan to quickly contain and recover from cyber incidents.
- Conduct an annual cyber risk assessment: Ensure all cyber controls are being administered properly and address new potential threats.
As fleets become more digitally integrated, the importance of cybersecurity cannot be overstated. From telematics to cloud platforms, every connected component introduces potential vulnerabilities. By understanding vehicle attack surfaces, investing in cybersecurity certifications, and implementing best practices, fleet operators can protect their assets, ensure operational continuity, and maintain the trust of customers and partners in an increasingly connected world.
Browse more resources in our library